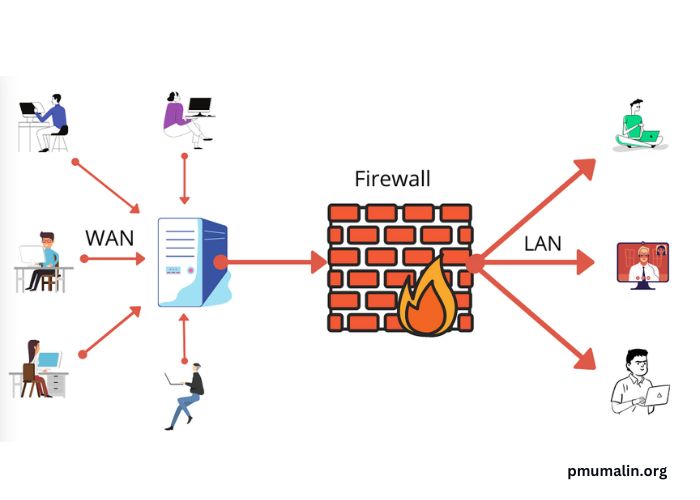
Introduction to Firewalls
In our increasingly digital world, protecting personal and sensitive information is more crucial than ever. A firewall serves as one of the paradigms of digital defense, acting as a primary shield in the complex battlefield of cybersecurity. These digital barriers are essential; they meticulously manage and regulate traffic between trusted and untrusted networks, erecting a fortress around your digital kingdom. Initially, firewalls addressed more straightforward tasks, focusing merely on granting or denying access based on preset rules. However, as the sophistication of cyber threats burgeoned, so did the sophistication of firewalls, morphing from mere gatekeepers into indispensable security allies in both personal and business contexts.
How Firewalls Function
Firewalls monitor the traffic that flows into and out of your network, scrutinizing each data packet to ensure it meets a predetermined set of security criteria. Essentially, they act as strategic checkpoints where data is vetted before passing through. By utilizing protocol rules such as packet filtering, proxy services, and stateful inspection, firewalls intelligently decide which data packets can move in or out of a network. Packet filtering involves examining the headers of packets, allowing them to pass based on the rules defined for IP addresses, ports, and protocols. Proxy services serve as mediators, conducting traffic flows on behalf of another computer, thereby cloaking the true identity of users within the network. Stateful inspection is more sophisticated, keeping track of the state of active connections and making flexible choices informed by the conditions and situation of the traffic. Through these multi-layered strategies, firewalls serve as vigilant guardians, ensuring integrity and confidentiality remain intact.
Types of Firewalls
Firewalls come in many types, each offering unique features and functionalities to fit various needs. Broadly, they can be categorized into network-based and host-based firewalls. Network-based firewalls are usually situated at the gateway of a network, acting as the first line of defense against incoming threats. They are designed to protect entire networks and provide a scalable solution for large operations. On the flip side, host-based firewalls are integrated into individual devices, providing a layer of security close to the source. It can be particularly beneficial for mitigating attacks that have bypassed other security checks.
Packet-Filtering, Proxy, and Stateful Inspection Firewalls
Diving deeper, firewalls can be classified based on their technology: packet-filtering, proxy, and stateful inspection firewalls. Packet-filtering firewalls enact elementary security checks by examining packets against a set of filters and allowing them through if they meet the criteria. While simple, they can be highly effective and are often embedded within other types of firewalls as a component of a more extensive system. Proxy firewalls act in an intermediary capacity, breaking the direct connection between sender and receiver to anonymize requests, thus providing an added buffer against direct attacks. Stateful inspection heightens the security measure by accounting for the state of each connection, offering decisions based on more than individual packets. Each type of firewall possesses its strengths, and often, a combination of different technologies is employed to create a robust line of defense against the multifaceted nature of modern cyber threats.
Importance of Firewall Protection for Businesses
In business, securing data against unauthorized access and maintaining the integrity of communication channels is vital. Robust firewall solutions provide a critical layer of security that shields sensitive information and enhances trust with clients and partners. These digital guardians oversee and regulate entry to corporate networks, preventing questionable actions that could result in data leaks, financial setbacks, and harm to reputation. Moreover, as enterprises continue to harness technology to drive growth, the role of firewalls in advanced threat prevention cannot be overstated. By minimizing potential attack vectors and managing internal traffic flows, firewalls enforce policies that uphold data security and compliance with industry regulations.
Firewalls in Personal Network Security
While businesses focus on large-scale protection, individual users also benefit significantly from implementing firewall security. By deploying firewalls on personal computers and devices, individuals can effectively guard against unauthorized external access. It is particularly vital in an era where personal data, including financial transactions, personal communications, and private files, can be tempting targets for cybercriminals. Firewalls offer an initial line of defense by blocking unapproved connections and alerting users to suspicious activities. Users are advised to regularly update and configure their hardware and software firewalls for added security. Adopting a layered defense strategy by integrating firewalls with additional security measures like antivirus software and proactive threat intelligence is key in safeguarding personal cyber territories.
Current Trends in Firewall Technology
As cyber threats evolve, so too do firewall technologies. Current trends highlight a shift towards adaptive and intelligent systems capable of responding to threats proactively. Integrating artificial intelligence and machine learning into firewall solutions revolutionizes security architectures by offering predictive analysis and deeper threat visibility. These advanced systems analyze patterns and anomalies within network traffic, providing real-time threat mitigation and learning from new attack paradigms. Such capabilities ensure that firewalls remain not just a static blockade but a dynamic, evolving element of cybersecurity strategy, capable of confronting the challenges of today’s digital landscape.
Common Firewall Myths Debunked
Despite widespread adoption, firewalls are often misunderstood, leading to common myths that warrant clarification. One such misconception is the belief that firewalls alone offer comprehensive security. While they are a crucial part of the security puzzle, firewalls must work with other cybersecurity measures to form a holistic strategy. Another prevalent myth is that all firewalls are created equal; in reality, different systems offer different features and levels of protection. Understanding these variances and selecting appropriate firewall solutions can significantly enhance security posture. Awareness and expertise in implementing varied security technologies and routine updates are essential in dispelling these myths and fortifying overall defenses.
Conclusion & Final Thoughts
In conclusion, firewalls are indispensable in the ongoing quest to secure our digital footprint against relentless cyber threats. They serve as vigilant barriers, allowing safe passage for legitimate data while blocking malfeasant incursions. By understanding and utilizing their full potential, businesses and individuals alike can bolster their defenses, guaranteeing the safety and confidentiality of their online resources. As technology progresses, so must our strategies, with firewalls fostering a safer, more secure online experience now and into the future. In this perpetual battle for cybersecurity, firewalls stand as a testament to our strides in protecting our virtual spaces.